Phishing
Phishing refers to sending an e-mail which tricks someone into clicking on a link or opening an attachment. The end goal of phishing is to steal valuable information, such as usernames and passwords.
The UNF Information Security Team values the assistance of the UNF community in our ongoing battle with phishing messages.
Most phishing messages are harmless if handled carefully. Below are some tips to help identify and properly react to a spam/phishing message.
Phishing messages often:
- Bad spelling and grammar: Simple phishing emails are often poorly written. If the content of the e-mail doesn't line up with what you'd expect from the sender, beware!
- Deceptive links: Move your mouse over any of the links in the e-mail, without clicking. You should see the address where the link will take you. If it's an e-mail from your bank, but the link doesn't display your bank's website, don't click.
- Sense of urgency: Is the e-mail claiming that you missed a package delivery, or telling you that your e-mail account will be suspended? Be careful - somebody may want to worry you into clicking on a malicious link. When in doubt, pick up the phone or type the address of the organization into your web browser.
- No name in e-mail: Is an e-mail starting with Dear Customer but not including your real name? Chances are the fraudster doesn't even know who the e-mail account belongs to. Don't click.
Don't get hooked! Don't bite on phishing attempts

Jane is reviewing her email when she comes across a strange message. It is from a bank that she doesn't have a bank account with, asking her to update her account information. It asks that she answer a few questions to validate her account due to recent fraudulent activity. A helpful link to a web page is included. Curious, Jane clicks on the link and is taken to a page that prompts her to enter her first name, last name, social security number, account number and password. Knowing that something is definitely wrong - she doesn't even bank there! - Jane closes the page and deletes the email.
Jane has just encountered a phishing attack. Phishing is an attempt to lure unwary consumers into divulging personal information such as credit card numbers, bank account information, passwords and Social Security numbers to scammers. In this case, Jane knew that something was up because she didn't bank where the email had purportedly come from. She correctly decided to not answer any of the questions and deleted the email. But what if the phishing attempt had been more convincing? Consider the following...
Joe is quickly scanning his email first thing in the morning. One message stands out, as it comes from his bank. Opening it, he reads how the bank has recently enacted new security measures designed to prevent criminals from impersonating Joe online and accessing his account. Joe is interested in this, as he relies heavily upon his account for online bill paying and automatic deductions. He likes the idea of adding security questions and other key security features. Reading further, Joe sees that in order to activate these features, he will need to answer a few questions to validate his identity and account. Joe clicks on the link provided in the email and watches as his browser opens the web page.
Knowing that he has to be careful about giving out his information, Joe looks for and finds the lock icon indicating that the session is protected by encryption. He also carefully looks over the page and can see that it does indeed look like his bank's home page. He even follows a few of the links on the page and scrutinizes the telephone numbers and email contacts provided for customer support and loan applications. Everything looks in order, so Joe returns to the initial page and fills in the fields asking for his name, account number, password and security questions. He clicks submit and relaxes as the page displays his information for verification and informs him that all security measures have been enabled.
Unfortunately for Joe, he has not given his information to his bank, but to a criminal. By the next day Joe's account has been emptied by electronic transfer to a bank account located overseas. Joe doesn't even know this until he receives his first overdraft notification and by then it is too late.
Phishing attacks range from very basic, crude attempts to get you to send information to someone by email, to elaborate, very convincing schemes involving multiple web pages, emails and seemingly genuine automated responses.
Tips
Phishing attacks range from very basic, crude attempts to get you to send information to someone by e-mail, to elaborate, very convincing schemes involving multiple web pages, e-mails and seemingly genuine automated responses.
So how do you protect yourself? Here are some easy tips:
- Do not reply to e-mail asking you for personal or financial information.
No reputable bank, credit union or company will ever ask you for sensitive information in an e-mail. When in doubt, contact the entity that sent it to verify it is genuine.
- Never trust any links contained in such e-mails. Always type in the web address of the the bank or company yourself.
This protects you from fake web addresses that appear to come from the real source, but actually redirect you to the scammer's fake web page. Remember that many of these fake web pages look very convincing and may contain actual links to some parts of the real organization's web site to appear legitimate.
- Use antivirus and antispyware software and keep it up to date.
This is a basic precaution, but it bears repeating. Some phishing emails contain software that can harm your computer or track your activities on the Internet without your knowledge. Having up to date antivirus and antispyware software can help protect against these types of attacks.
- If you believe you've been scammed, file a complaint with the Federal Trade Commission (FTC) , then visit the FTC's Identity Theft website.
Victims of phishing can become victims of identity theft. While you can't entirely control whether you will become a victim of identity theft, you can take some steps to minimize your risk. If an identity thief is opening credit accounts in your name, these new accounts are likely to show up on your credit report. You may catch an incident early if you order a free copy of your credit report periodically from any of the three major credit bureaus. See www.annualcreditreport.com for details on ordering a free annual credit report.
Don't forget to change your account password if you think it may have been compromised. This is especially true if you have responded to a phishing attempt - change your password right away.
Outlook
-
Preview Link before Clicking
In Outlook, you can view a link before you click on it. Do not trust that what is visible is the actual destination link! Move your mouse over any of the links in the e-mail, without clicking. You should see the address where the link will take you.
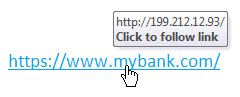
If it's an e-mail from your bank, but the link doesn't display your bank's website, don't click.
-
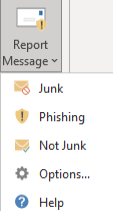
Phish Alert Outlook Add-In
If you receive a suspicious message in the future that doesn't appear to come from a UNF address, you can safely delete it or use the Outlook Phish Alert add-in to report the message as phishing to Microsoft. This helps all users of Microsoft email identify and block unwanted/malicious emails. By reporting it to Microsoft, you're helping to ensure that you and others receive fewer spam and phishing messages in the future.
Phish Alert Outlook Add-In (Desktop Application)
Phish Alert Outlook Online (Web) - Found under the "More actions" drop down.
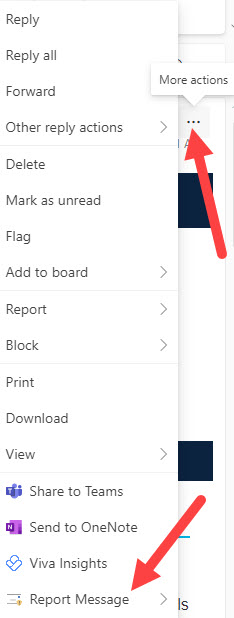
Found near the bottom of the list
If you have any questions, please email ITSecurity@unf.edu
Examples
-
Example 1
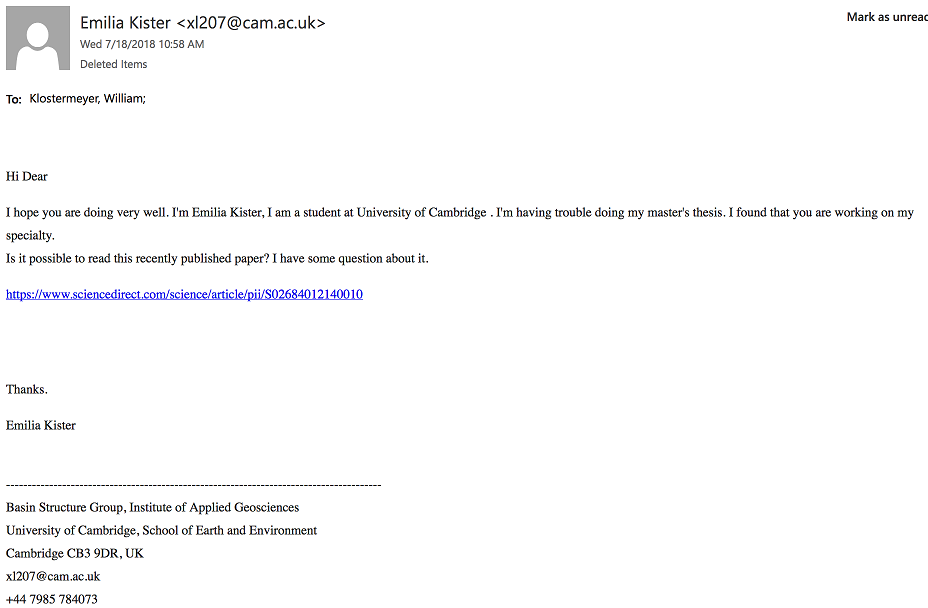
The image above shows an example of a phishing email that is sent from an external email address. It contains bad grammar, external links, and attempts to lure the recipients to click the link by asking for help by pretending the content is in their specialty. Notice there is no proof that the content is intended for their field.
-
Example 2
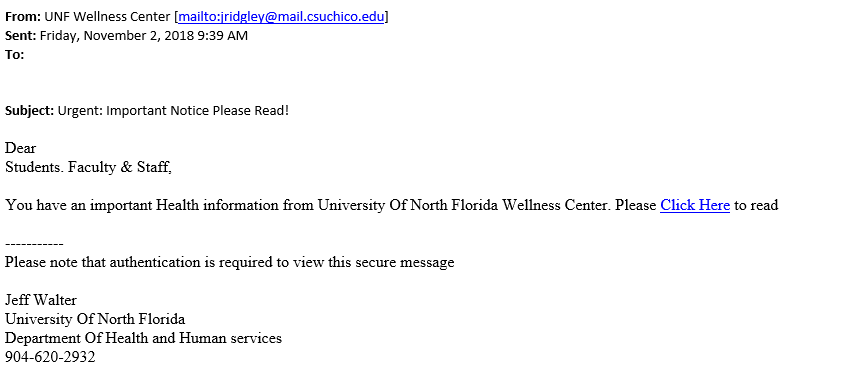
The image above shows an example of a phishing email that is sent from an external email address trying to spoof the UNF Wellness Center. It also contains bad grammar, external links, and asks about personal information.
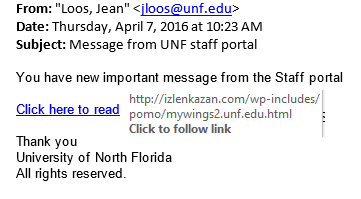
The image above shows an example of a compromised UNF user account. This type of phishing email is rare as the sender was from an internal email address. The email does contain bad grammar, external links, and uses language not commonly used at UNF. (Staff portal vs. mywings)
How to use the Report Message feature in outlook
If you are ever unsure about an email being legit, you can safely delete it or use the Report Message add-in to report the message as phishing to Microsoft. This helps all users of Microsoft email identify and block unwanted/malicious emails. By reporting it to Microsoft, you're helping to ensure that you and others receive fewer spam and phishing messages in the future.

If you are using the mobile version of outlook, select the three dots in the top right. The pop out screen will have an option to mark as phishing.

The Report Message feature in Outlook can assist in protection against phishing attacks. Report malicious emails to Microsoft, helping to fight security threats. If a suspicious message appears to come from a valid UNF email address, email IT Security a copy of the header data as well as a copy of the email itself.
Along with the feature, if a suspicious message does appear to come from a valid UNF email address, please send IT Security a copy of the header data as well as a copy of the email itself.
